In the previous post, I've talked about guessing your password. Now I'm gonna cover another case.
Stealing Your Key
Now you have a super secure password and you feel calm and safe, right? But thieves are in ambush. Whenever you use your password in an app or online site, they can steal it: this is a man-in-the-middle attack.
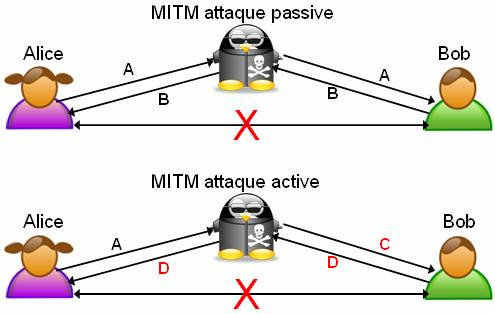
It can be possible if your credentials are transmitted in plain text through a unencrypted connection (for example the WiFi of hotels or airports) but there are some situations where it succeeds even over a secure connection (SSL/TLS).
Of course, your password can also be stolen if the thief can access a website database. You may argue that if someone has the access to a server content, it should not care about passwords: all your data are in his hands. This is not completely true: hackers know that many people use the same password across different services, so, for example, knowing your email password can lead them to access also your bank account. This is why it's a good practice to use a different password for every service.
Nowadays, I don't think any online service is crazy enough to save password in plain text. Simple hashing has been quite common in the past years, until someone discovered that it can be overtaken by hash dictionaries and rainbow tables. For this reason, a bit of salt has been added to plain hashing. Salting, in this situation, means adding few random characters (called "salt") to passwords before hashing. To increase security, salts are stored in a separate database.
In any case, a weak password can easily be discovered, no matter the server security, so the suggestion is always the same: use strong passwords!
The third and last part of this series is here.
Image by Martial Régereau taken from Wikimedia Commons licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license.
